owasp thick client application testing|owasp vulnerability checker : wholesaler The OWASP Thick Client Application Security Verification Standard (TASVS) Project aims to establish an open standard for securing thick client applications. Mary-Belle Kirschner (born 23 October 1999), better known as Belle Delphine, is a South African-born British media personality, pornographic actress, model, and YouTuber. Her social media accounts feature erotic and cosplay modelling, sometimes blending the two together. Her online persona began in 2018 through her cosplay modeling on Instagram. Her posts on the platform were often influ.
{plog:ftitle_list}
webPágina · Serviços funerários e cemitério. +55 51 3715-3868. Funerária Halmenschlager Santa Cruz do Sul, Santa Cruz do Sul. 1.353 curtidas · 4 falando sobre isso · 1 esteve aqui.
The OWASP Thick Client Project is a standard awareness document for developers and security analyst. It represents the most common security risks identified in thick client applications. .The OWASP Thick Client Application Security Verification Standard (TASVS) .
Companies should adopt this document and start the process of ensuring that their .The OWASP Thick Client Application Security Verification Standard (TASVS) Project aims to establish an open standard for securing thick client applications. Companies should adopt this document and start the process of ensuring that their . In this article, we will learn about thick client applications, their vulnerabilities and ways to carry out security assessment of these applications. A thick client, also known .
thick client security testing
OWASP Based Checklist 🌟🌟. 80+ Test Cases 🚀🚀. Notion link: https://hariprasaanth.notion.site/THICK-CLIENT-PENTESTING-CHECKLIST-35c6803f26eb4c9d89ba7f5fdc901fb0. INFORMATION GATHERING. The most common vulnerability in thick client applications is SQL Injection. According to OWASP, injection flaws, such as SQL, NoSQL, OS and LDAP injection, occur when untrusted data is sent to an interpreter as part of a . First challenge: enabling a button. Information gathering phase. Traffic analysis. Attacking thick clients applications. Reversing and patching thick clients applications. Common vulnerabilities. Thick clients applications .
Thick client security assessment can be divided into below four major parts. Static test. Dynamic test. System test. Network test. Static test. Here we observe and test for potential issues. This post highlights different tools and approaches for testing thick client applications for vulnerabilities. Thick client testing tools have remained the same over time while new frameworks / technologies have given rise to . Thick client penetration testing involves various methods tailored to different aspects of application security: Source Code Analysis: Examining the application’s source code to identify vulnerabilities and coding errors. Binary . Thick clients can be referenced by many names: Fat Clients, Rich Clients or even Heavy Clients. Such applications follow a client-server architecture and can be developed using various programming .
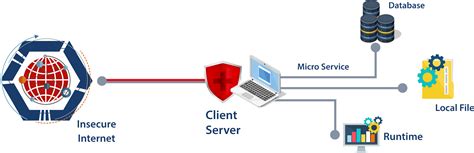
Common examples of thick client applications are video games, audio video editing tools, Microsoft Office, etc. Thick client security assessment can be divided into below four major parts. Static test The Hybrid Infrastructure on which the Thick Client Application usually resides poses more security challenges than web-based thin clients. To put it in simple terms, the Thick Client Application runs on the user’s system, . OWASP TOP 10 Rank; SANS Top 25 Rank, and; References; . As evidence, the Thick client application testing services provider provides a Letter of Attestation, which certifies your organization’s security level based on penetration testing and security assessments. This letter also serves various objectives, such as validating security levels .
As we have understood what thick client is and its architecture, now we’ll move on to the penetration testing approach. We have shown some vulnerabilities of thick client. Starting checks (Enumeration) Application Architecture Business Logic; Platform Mapping Understanding Application & Infrastructure; Languages and Frameworks Thick clients are the applications that must be installed on desktops/laptops or servers. These applications can be run on the internet or without the internet. . Test for OWASP TOP 10 web vulnerabilities; Test for OWASP TOP 10 API vulnerabilities; 5) Code Review. Use Code Scanner to scan source code for security weaknesses;
When an application is running on an untrusted system (such as a thick-client), it should always connect to the backend through an API that can enforce appropriate access control and restrictions. Direct connections should never ever be made from a thick client to the backend database. Implementing Transport Layer Protection¶
To test a thick client application the most important task is intercepting the requests fired by the application. On the basis of this benchmark, it can be classified as follows: 1.Our application penetration testing follows a structured methodology based on industry standards such as the OWASP Testing Guide, PTES (Penetration Testing Execution Standard), OSSTMM (Open Source Security Testing Methodology Manual), OWASP Mobile Security Testing Guide (MSTG), and NIST SP800-115.Thick client applications are more complicated and customized as compared to web or mobile applications.This makes the pen testing approach for thick client applications very different. A very specific approach to testing these applications is followed after understanding the application in terms of technologies used, functionality, behavior .
OWASP Foundation Respository. Contribute to OWASP/www-project-thick-client-security-testing-guide development by creating an account on GitHub.Client-side; API; Each test in each domain has enough information to understand and run the test including: . The WSTG document is widely used and has become the defacto standard on what is required for comprehensive web application testing. An organization’s security testing process should consider the contents of the WSTG, or have . The OWASP Top 10 includes a number of tests that are applicable to thick client applications. In addition, the OWASP provides associated tools and information. One of the most important tools for testing thick client applications is Echo Mirage. This tool can help you intercept and manipulate TCP traffic on a remote computer.OWASP ZAP, on the other hand, focuses on web application security and provides a comprehensive set of tools for testing thick client applications. Its automated scanning capabilities help identify common vulnerabilities, such as cross-site scripting (XSS) and SQL injection, in both the client-side and server-side components of the application.
The OWASP Testing Guide chapter on SSL/TLS Testing contains further information on testing. There are a number of online tools that can be used to quickly validate the configuration of a server, including: . However, public key pinning can still provide security benefits for mobile applications, thick clients and server-to-server communication. Diagram 1.2 (3) the thick client can be divided into two parts as shown below: (3.1) exe files or (3.2) web-based launcher like a java-based application.To learn the Thick Client Application Penetration Testing concepts by practicing, it is important to have a lab where we can practice everything in a legal environment. Vulnerable Application Design: DVTA application is developed using C#.NET in Microsoft Visual Studio. This client communicates with SQL Server and an FTP Server that are running . Thick client applications can be developed using Java, .Net, C/C++, etc. A thick client may follow two-tier architecture or three-tier architecture. In two-tier architecture, the thick clients directly access the back-end database via the internet. In .
The OWASP Thick Client Project is a standard awareness document for developers and security analyst. It represents the most common security risks identified in thick client applications. Organizations should adopt this document to ensure that their applications minimize these common risks. Using the .OWASP is aware of the Application Vulnerability Scanner . Automatic Penetration Testing for Applications & API Schema Penetration Testing: Mayhem for API: . out of band detection) and other OWASP Top 10, and more high-risk vulnerabilities. Even newer vulnerabilties such as Client-Side Prototype Pollution are included. Probely:
Echo Mirage: It is an all-rounder testing tool for thick clients. Echo Mirage, like Burp / OWASP Zap, enables the interception of client-server traffic. 2. . Phases in thick Client application pen testing Information Gathering . In this phase, we need to gather details about the application. This will help us understand the functionality and . There is an OWASP thick client top 10 but it is still in development. Here is a methodology framework to follow: Enumeration: Identify language & framework, architecture, . So, for example, in this session, we focus on the Windows-based client application. If you're testing a Linux- or a Mac-based client, you’ll need a proper setup. So .
thick client applications vulnerabilities
BreachLock thick client application penetration testing identifies vulnerabilities and security weaknesses of software applications that run on a user's local device, such as a desktop computer or mobile device, to communicate with a server or remote system over the network. . BreachLock adheres to OWASP (Open Application Security Project .Server-side attacks in thick client applications are similar to web application attacks, and penetration testers should pay attention to the most common ones including most of the OWASP Top Ten. Methodology for specific attacks
The Security Testing Guide (WSTG) Project produces the premier cybersecurity testing resource for web application developers and security professionals. Store Donate Join. This website uses cookies to analyze our traffic and only share that information with our analytics partners. . Version 1.1 is released as the OWASP Application .
The OWASP Top 10 is the reference standard for the most critical web application security risks. Adopting the OWASP Top 10 is perhaps the most effective first step towards changing your software development culture focused on producing secure code. . Number of applications tested; Type of testing (TaH, HaT, Tools) Primary Language (code .
Thick Client VA/PT Audit by Briskinfosec with expertise vulnerability assessment and penetration testing to secure your thick client applications. Home HOME Latest Press Release . OWASP is the blueprint for testing the web application security controls. It is safe to say that it helps the developers to develop application.
thick client applications security
owasp vulnerability checker
refractometer buy ireland
Resultado da This is the wind, wave and weather forecast for Zeebrugge in Flemish Region, Belgium. Windfinder specializes in wind, waves, tides and weather reports .
owasp thick client application testing|owasp vulnerability checker